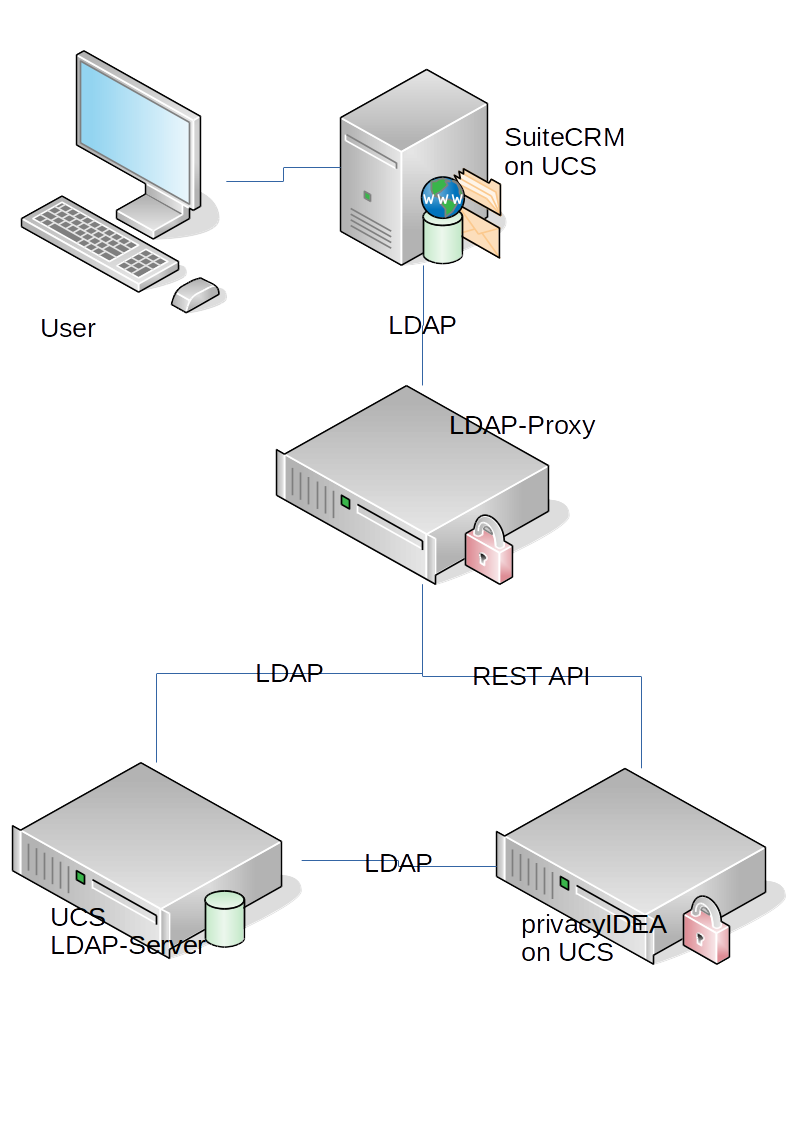
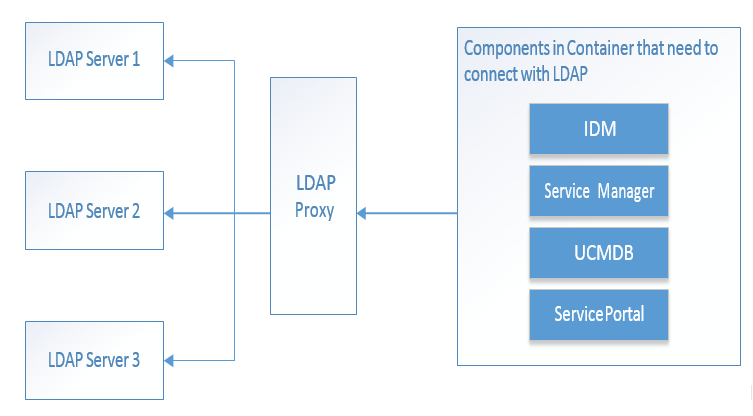
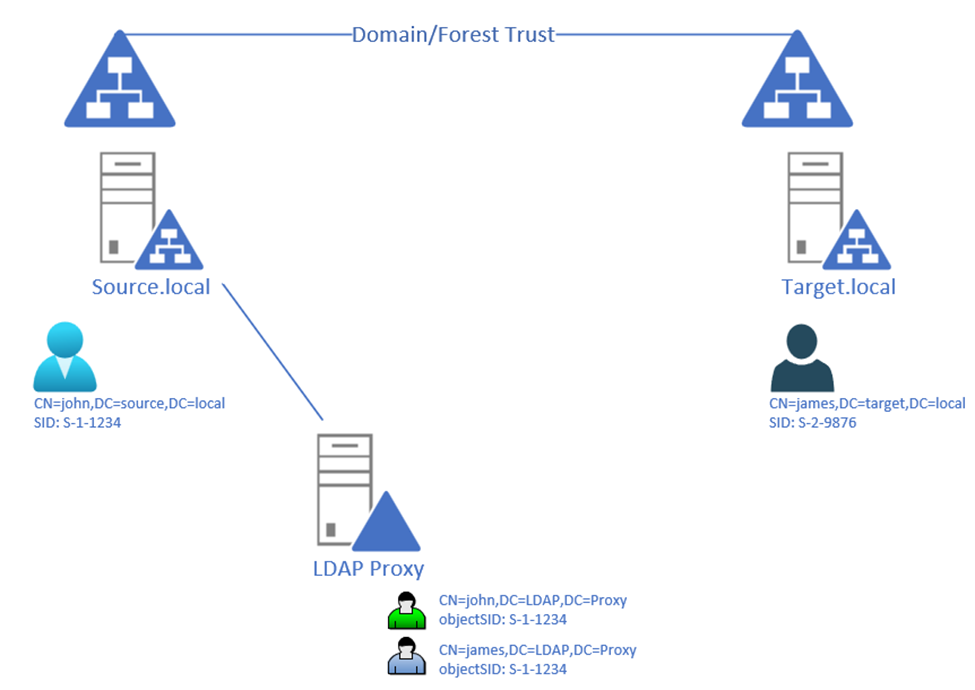
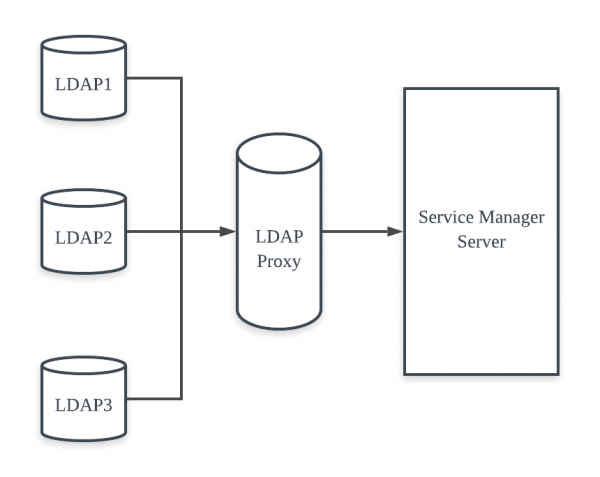
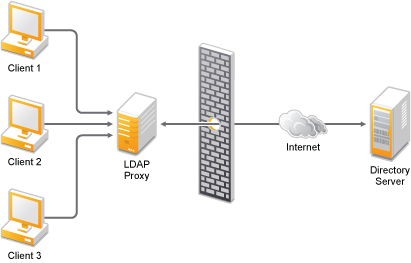
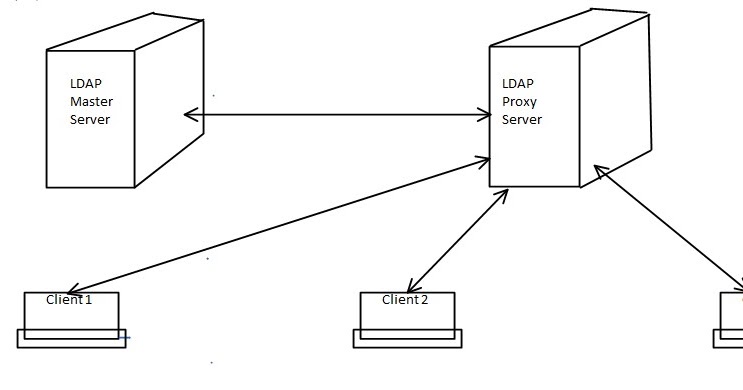
Modernizing your B2C Portal Security - LDAP Proxy for Cloud Identity - IBM Security Identity and Access
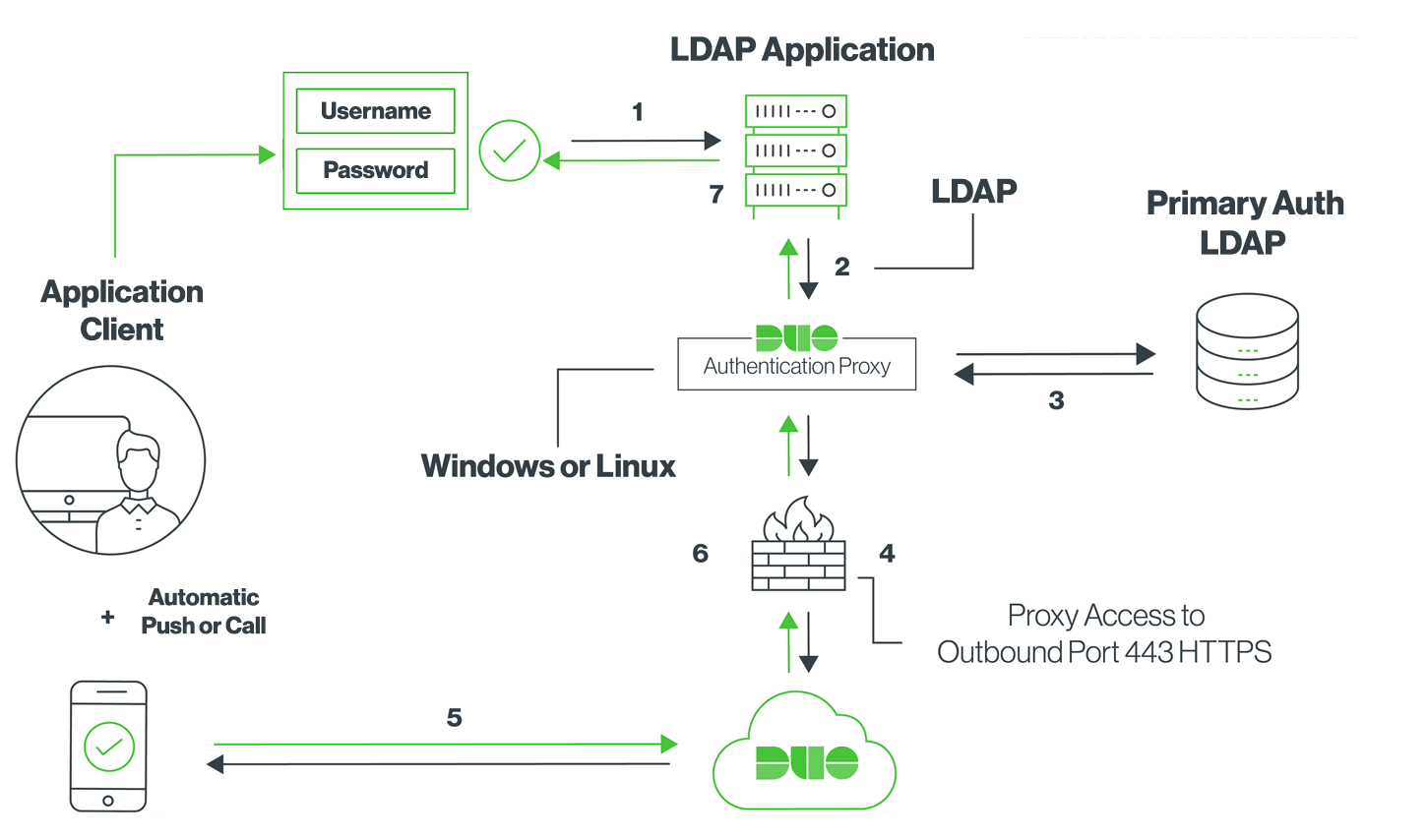
What are the differences between [ad_client] and [radius_client] Duo Authentication Proxy configurations?
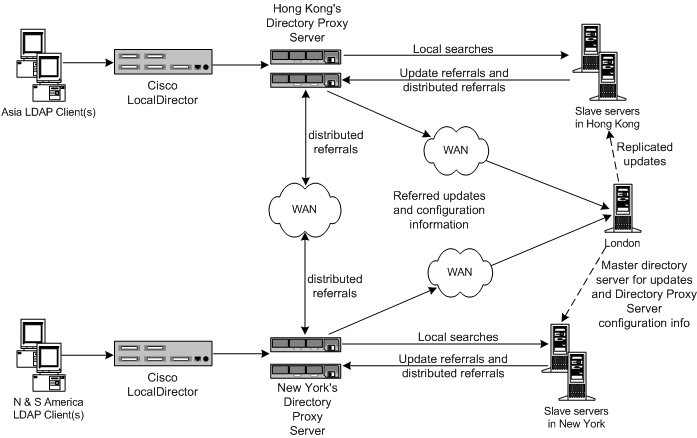
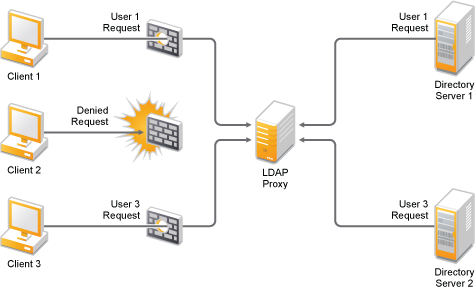
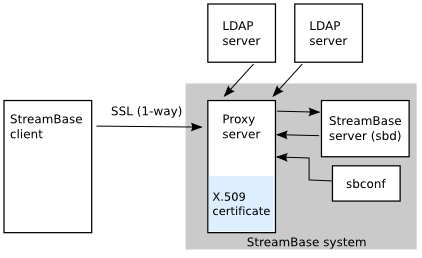
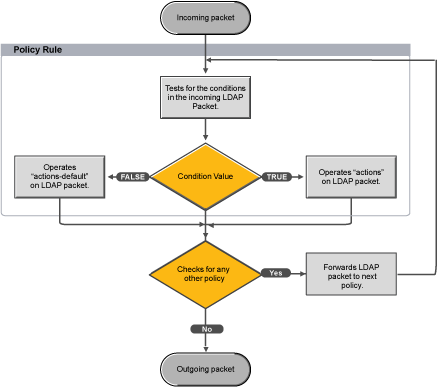
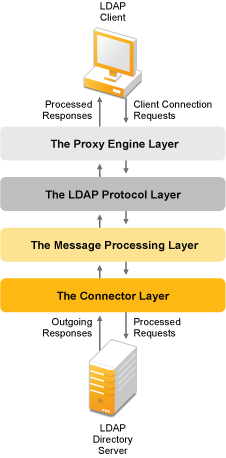
Sun ONE Directory Proxy Server Admistrator's Guide: Chapter 2 Sun ONE Directory Proxy Server Deployment Scenarios