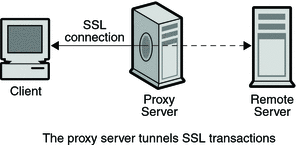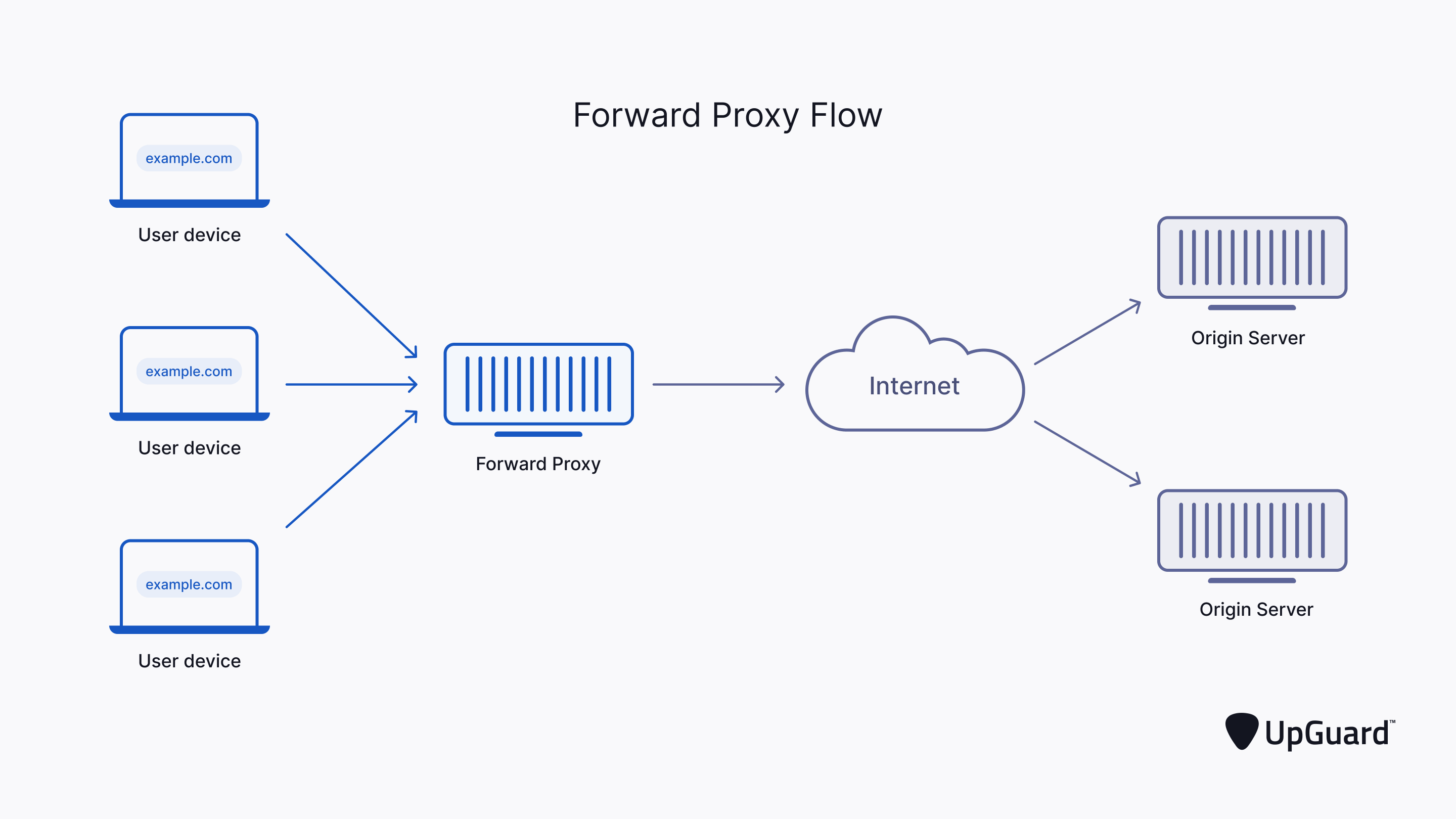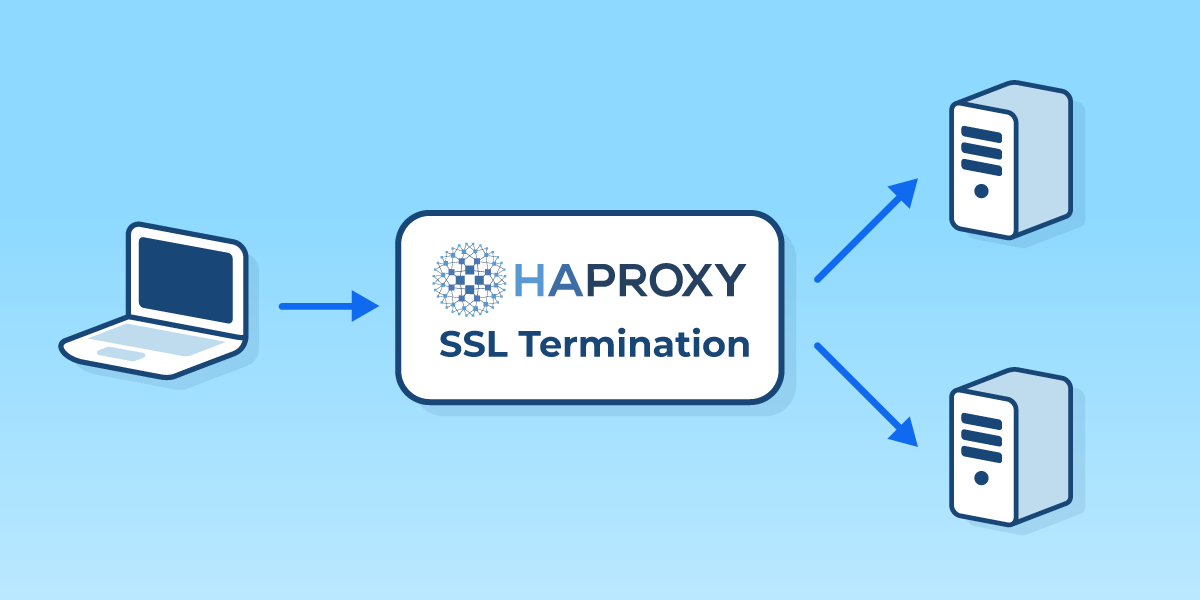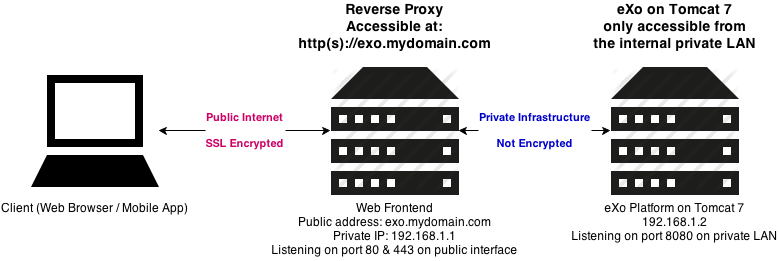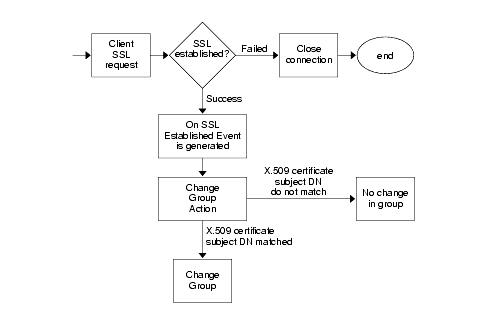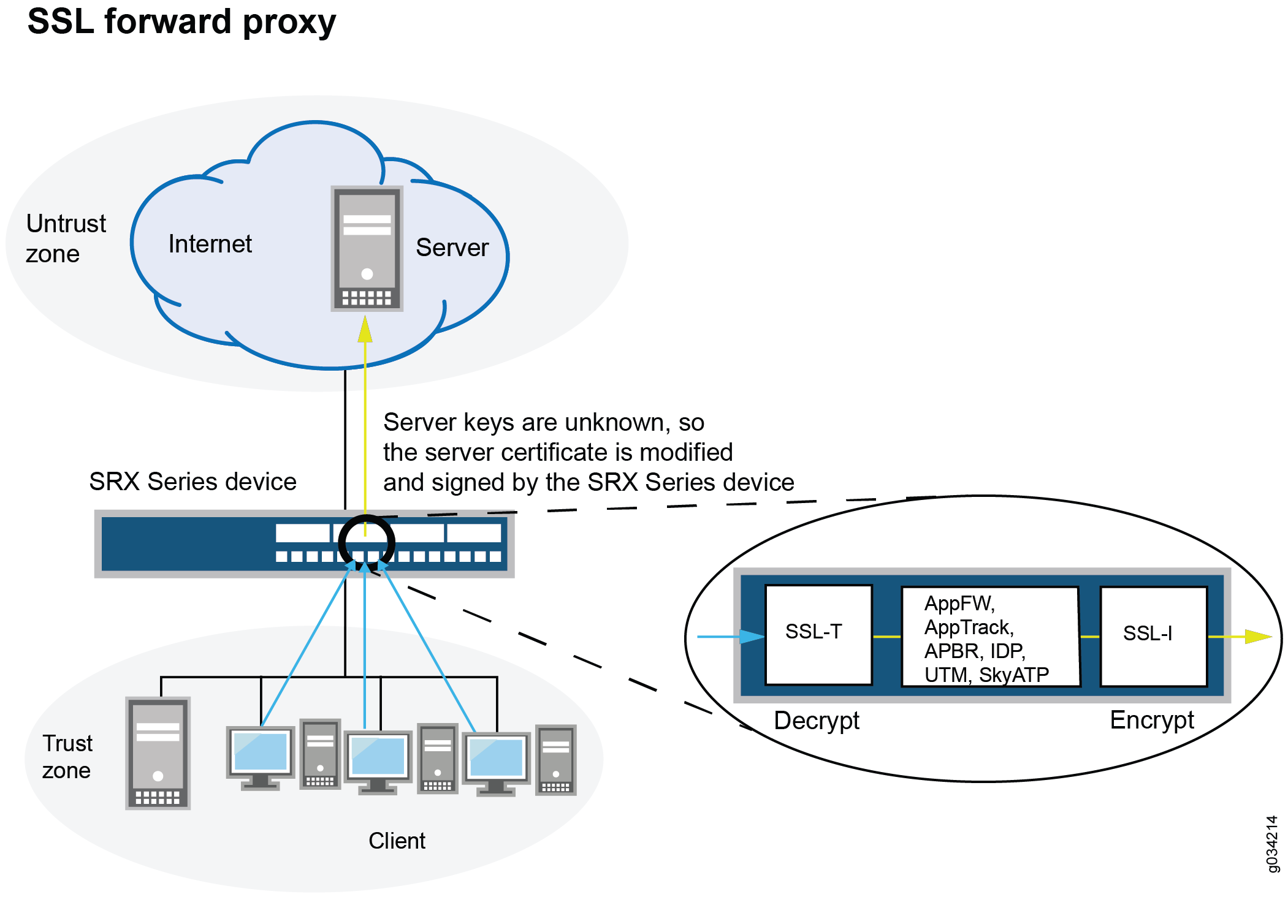
How to Configure Security Policies to Allow SSL VPN - Huawei Firewall Security Policy Essentials - Huawei
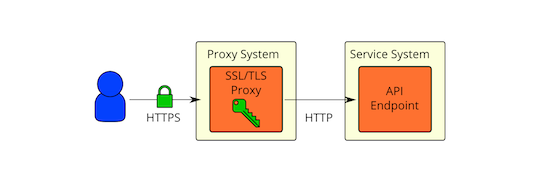
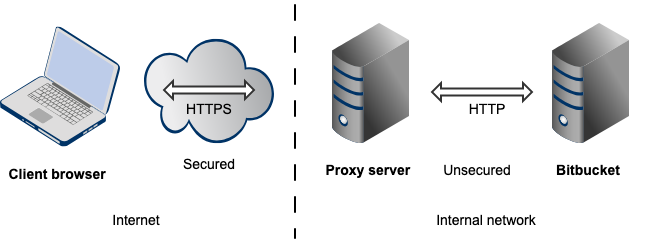
GitHub - sonertari/SSLproxy: Transparent SSL/TLS proxy for decrypting and diverting network traffic to other programs, such as UTM services, for deep SSL inspection

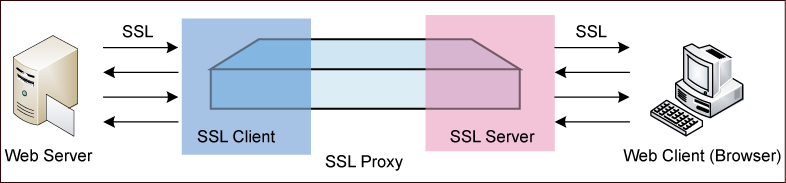
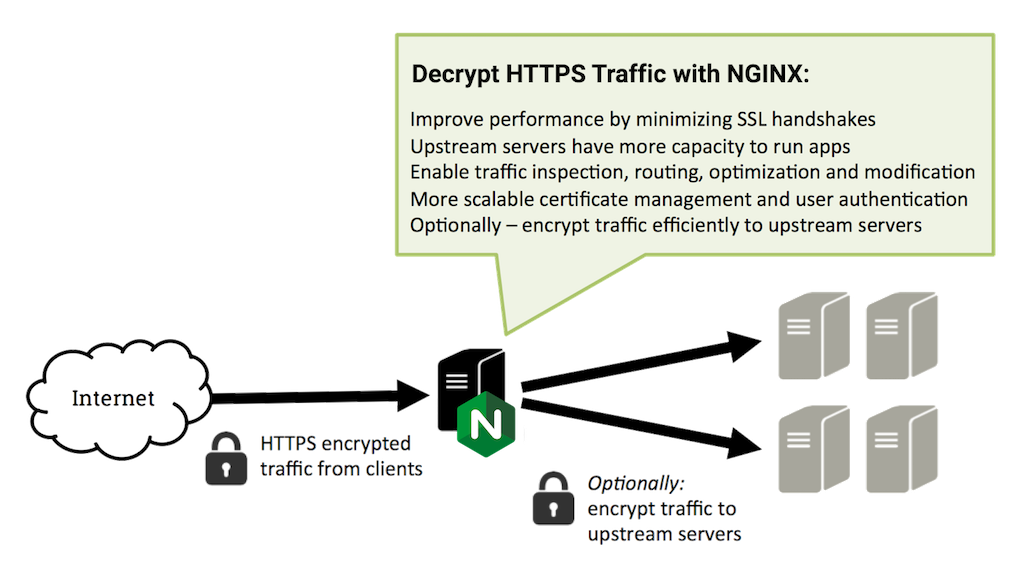
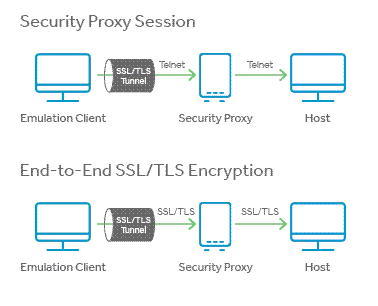
Reverse Proxy Server IT Secure Sockets Layer Ssl Proxy Server And Its Architecture Ppt Inspiration Outline PDF - PowerPoint Templates